Tuesday, June 26, 2007
Database security: protecting sensitive and critical information
Monday, June 18, 2007
Introduction:
What is school of internet?
Entrance registration
( http://www.soi.wide.ad.jp/aboutsoi/aboutsoi_e.html for details)
Tribhuvan University is one of the partner organizations of this project. Center for Information Technology (CIT), Institute of Engineering (IOE) is handling this project as a member. CIT has SOI server control room and SOI lab to conduct virtual classes. Series of lectures (eg: Advanced Internet Technology, Object Oriented Software Development, Disaster Management, Bio-energy etc…) are being conducted. (Follow http://www.soi.wide.ad.jp/soi-asia/lecture.html to see all lectures conducted till now). Each site has more than two formal operators well trained by the project with responsibilities to handle SOI server and conduct classes. Operators announce class time and course title to students, lecturers and professors through notices. The presentation is being broadcasted live from the central (any one member university, mostly from SFC Japan) to all universities and at the end of the presentation; students can join to the question/answer section through audio and video conferencing. Students, teachers, professors from any universities, schools and campuses can join on this class.
 In order to develop Internet infrastructure in low cost and short span in the partner sites, and develop distance education environment on the infrastructure, SOI Asia project designed
In order to develop Internet infrastructure in low cost and short span in the partner sites, and develop distance education environment on the infrastructure, SOI Asia project designed1) Lecturer site
2) Gateway site and
3) Student site
The lecturer site can be built anywhere as long as it has sufficient bandwidth to carry lecture video and audio in good quality to the gateway site.
Receive-only satellite antenna has been used at the student site using UDLR (UniDirectional Link Routing, RFC3077) technology. This technology enables the Ethernet packets to go through 13Mbps AI3 link and come back through existing Internet infrastructure such as telephone line or ISDN. This technology is realized by using special UDLR box and normal router based on FreeBSD. By using this environment, it is possible to deliver good quality video and audio to the student site, and get feedbacks from the student site through various applications based on their Internet infrastructure.
Mirror servers using Linux system are placed at the student site so that they can refer to their mirror servers when seeing the archived lectures, hence they don't have to connect to remote/overseas original server. Figure below shows the network configuration overview.
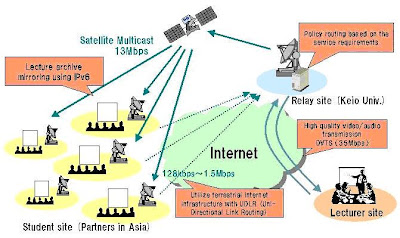
Three points in application design:
1) The stream can be multicast so that we can deliver lecture stream to multiple partners in Asia 2) The stream can be delivered to places without existing Internet infrastructure and
3) Interactive session based on student site's Internet connection is possible.
DVTS (Digital Video Transport System, RFC3189) or Polycom (video conferencing system) has been chosen for the connection between the lecturer site and the gateway site, and Windows Media Player or VIC (VIdeo Conference Tool) / RAT (Robust Audio Tool) for the connection between the gateway site and the student site. Various applications are being used such as VIC/RAT, Internet Relay Chat, Bulletin Board, MSN Messenger for the feedback from the student site to the lecturer site. The student site can decide which application they will use based on their Internet infrastructure.
Importance in developing countries
This is a call for a "Grand Challenge" project for achieving truly global connectivity. For over a decade, this project has hypothesized that the Internet could raise the quality of life in developing nations. Internet infrastructure is rapidly growing in Nepal. Growth in Information and Communication Technology would definitely improve the education quality. This is the age of globalization. So world’s education standards must globalize. Such projects have major contribution to globalize world’s education standards by conducting online live education which includes technologies of developed countries and share different countries education standards.
This is not to say the activity of the past decade has been a waste. The project has demonstrated the value of the Internet and raised awareness. The United Nations and the administrations of nearly all nations have acknowledged the potential of the Internet. The way has been paved, and it is time to act on what we have learned.
References
http://www.soi.wide.ad.jp/
http://portal.unesco.org/
Thursday, June 14, 2007
to downlod softflowd please follow the link: http://www.mindrot.org/files/softflowd/softflowd-0.9.8.tar.gz
PGP Signature is: http://www.mindrot.org/files/softflowd/softflowd-0.9.8.tar.gz.asc
Thanks Damien Miller for such tools necessary for network/system engineers like me.